InfoWAAP is currently in beta mode. To join the beta, contact the Gcore support team.
TipAfter you enable WAAP, all traffic will be diverted to our network, and it may cause a temporary disruption for your users. We recommend setting up Gcore WAAP during a low-traffic period to minimize the impact.
Step 1. Create a CDN resource
To secure your web application and APIs with Gcore WAAP, it’s necessary to create a CDN resource associated with your website’s origin. If you also need to add an SSL certificate, check out the Add an SSL certificate to deliver content over HTTPS guide.InfoWhen configuring a resource, you need to update your domain’s DNS records so they point to our network. This is necessary to allow all traffic to pass through WAAP.
If you don’t have Gcore CDN configured, follow the instructions from this guide: Create a CDN resource for the entire site.
Step 2: Enable WAAP in CDN resource settings
Once your CDN resource is set up, you can activate WAAP protection for it. Refer to the Protect CDN resources with Gcore WAAP guide for detailed instructions.Step 3: Use WAAP in monitor mode
After you enable WAAP, it will be automatically set to the monitor mode. In this mode, we’ll inspect all incoming requests but won’t take any action. It’s best to use monitor mode for several days before enabling the protect mode to make sure that all security settings work correctly. Completing this step is important because it allows you to analyze requests and test the WAAP behavior before you fully activate it.WarningIn monitor mode, all traffic is allowed to your domain, regardless of configured security rules and policy groups. This mode is only recommended for testing WAAP settings.
Step 4: View your domain traffic
While keeping WAAP in monitor mode, you can view all logged requests and check the corresponding actions that the WAAP will take once you put it in the protect mode. Go through the analytics pages to detect common traffic patterns and understand if the current configuration requires any adjustments. For instance, you can find information about incoming web requests on the WAAP analytics page in the Requests table: 1. In the Gcore Customer Portal, navigate to WAAP > Domains.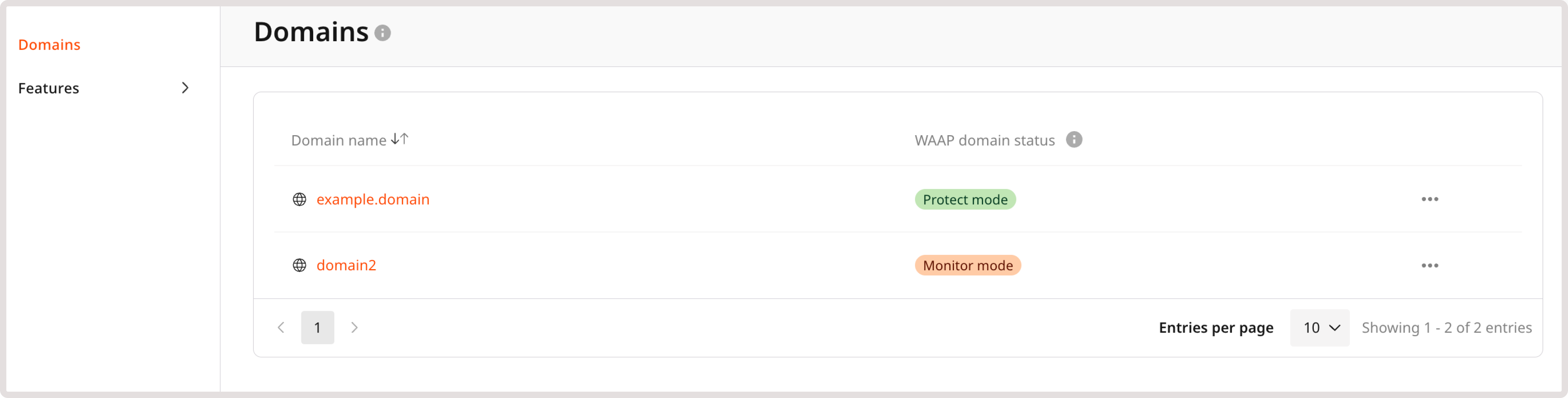
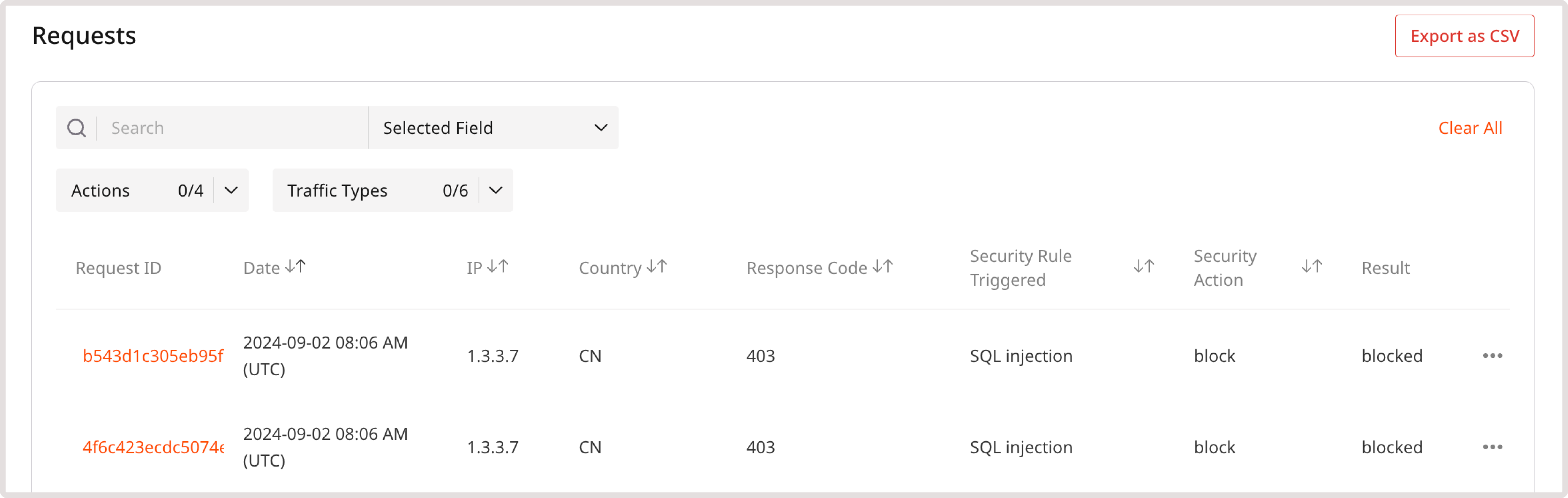
- Traffic types : View requests based on the rule that triggered the request.
- Policy – Blocked or Policy – Allowed : View requests that triggered our predefined policy groups.
- Select Custom Rule – Blocked or Custom Rule – Allowed : View requests that triggered custom rules created by your account users.
InfoPolicy - Blocked and Custom Rule - Blocked are the default filters automatically displayed for the table.
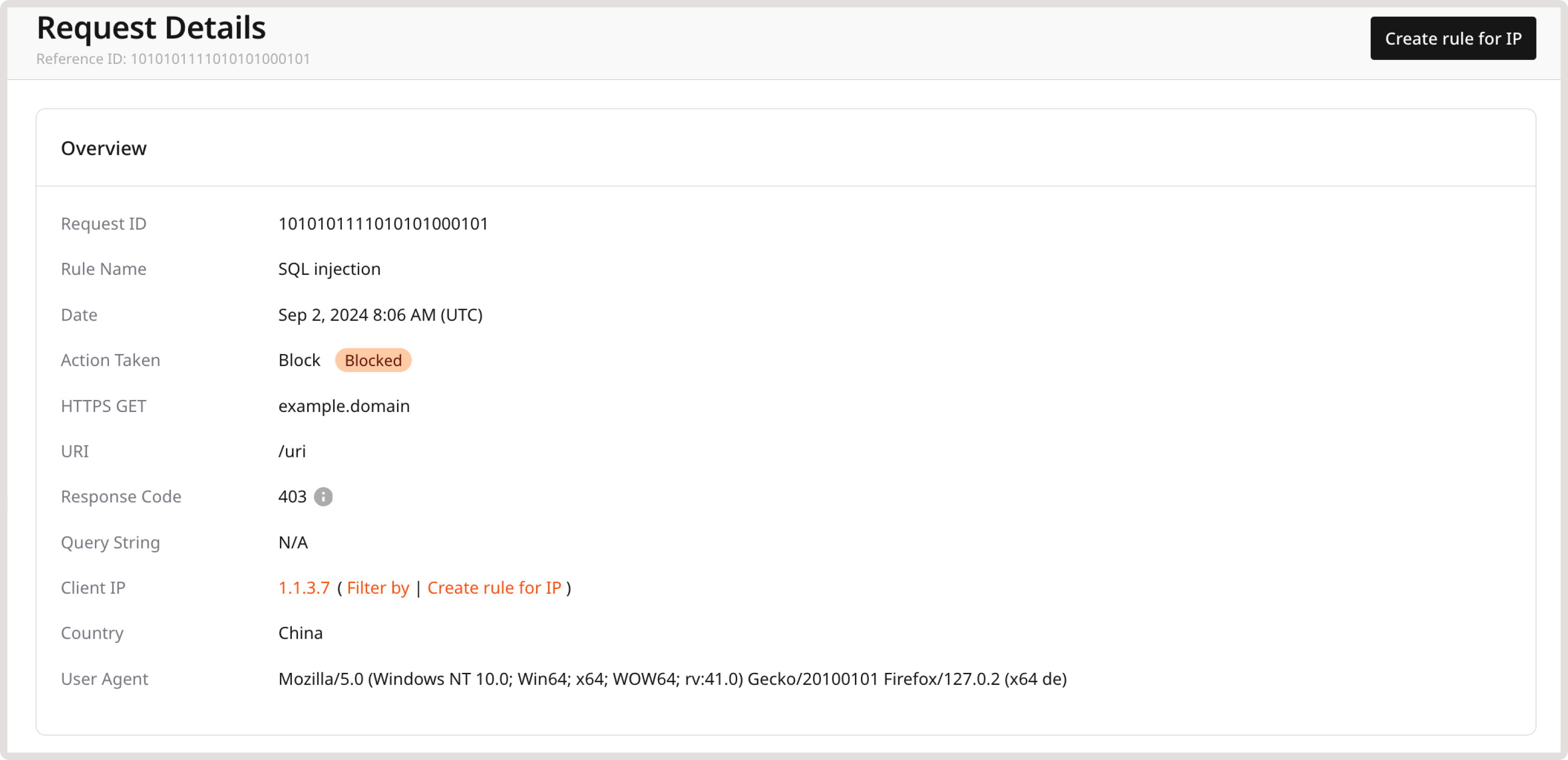
Step 5: Test your WAAP configuration
To achieve the desired WAAP behavior, we recommend that you navigate through your website as both a user and administrator. Navigating the website will generate entries in the Requests table. You can use this information to determine if you need to create Firewall rules or custom WAAP rules for some requests and let them access your website’s content. Specifically, review requests that relate to:- Your origin IP : IP address assigned to your device.
- Your office IP : IP address assigned to your device within your office’s network.
- Your workstation IP : IP address assigned to a workstation or specific computer in a network.
Step 6: Allow admins, bots, and CMS
Before the WAAP is in protection mode, you need to ensure that critical IP addresses, content management systems (CMS), and common automated services are allowed to make successful requests. Check the WAAP policy groups for a full list of security policies and their detailed overview.Allow admin IP addresses
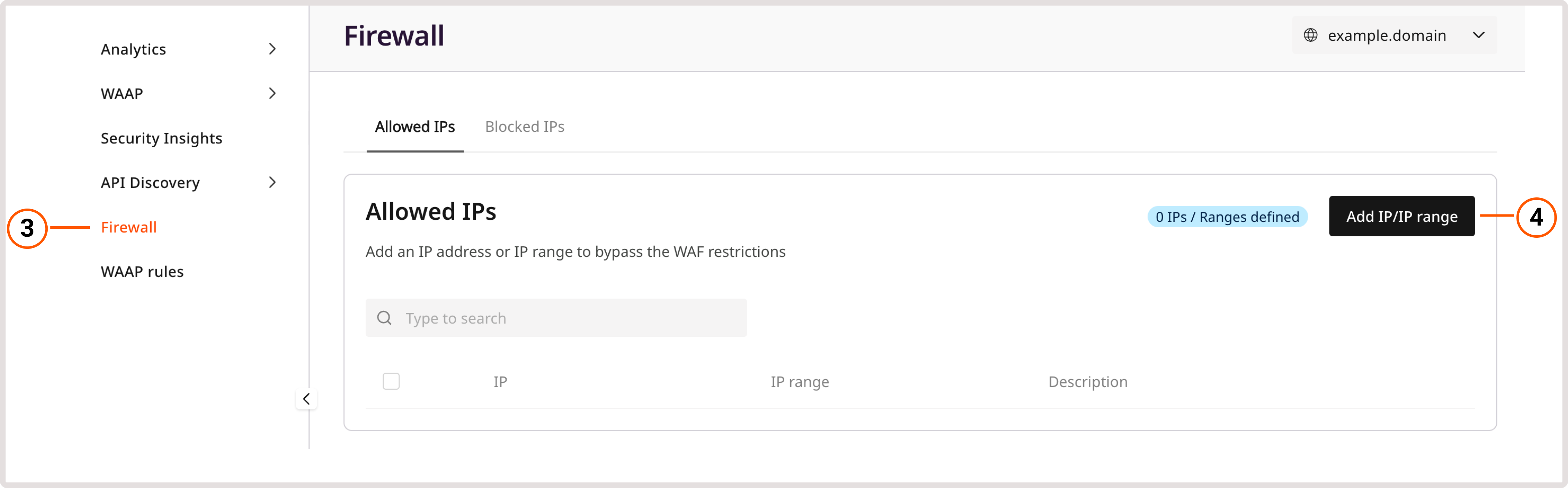
If your domain doesn’t use a CMS, we highly recommend allowlisting the site administrator’s IP address: 1. In the Gcore Customer Portal, navigate to WAAP > Domains.
Allow CMS
If you use content management systems, such as WordPress, allow traffic for CMS admins: 1. In the Gcore Customer Portal, navigate to WAAP > Domains. 2. Find the needed domain and click its name to open it. You’ll be directed to the Policies page. 3. In the sidebar, click WAAP. 4. On the Policies page, find CMS protection, and then allow traffic for a desired content management system by enabling a toggle next to it.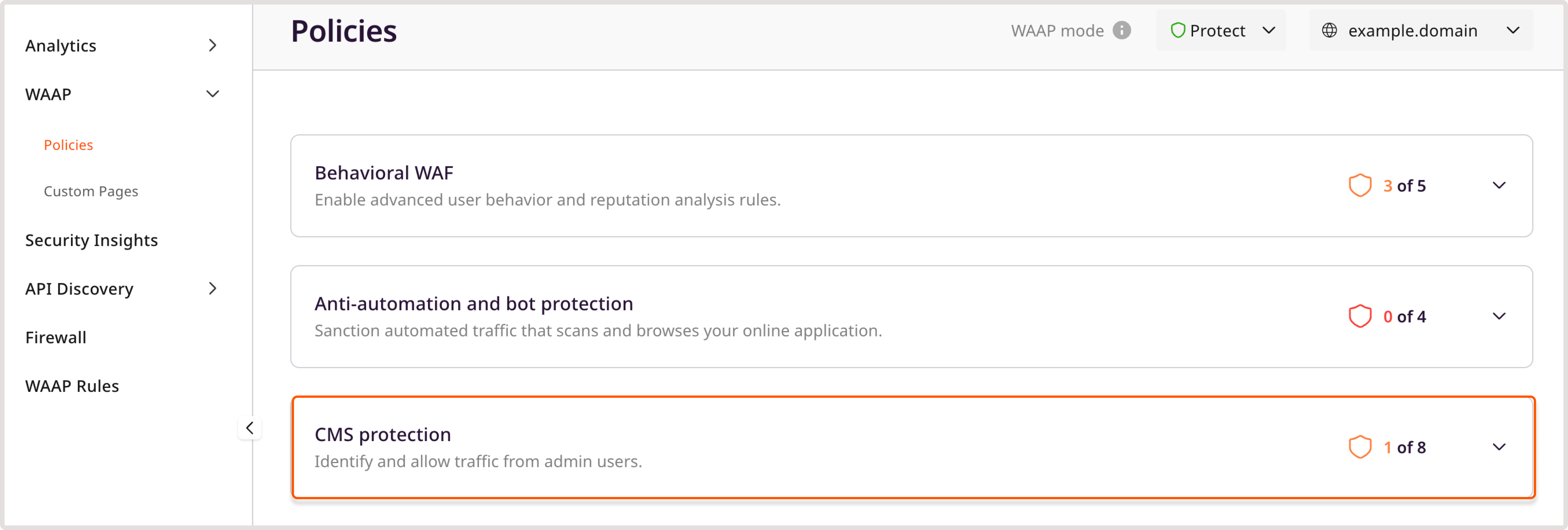
TipThe WordPress WAF ruleset policy is enabled by default.
Allow common automated services
Follow these steps to allow crawlers, scanners, monitoring bots, and similar tools to access your website: 1. In the Gcore Customer Portal, navigate to WAAP > Domains. 2. Find the needed domain and click its name to open it. You’ll be directed to the Policies page. 3. Click the Common automated services to expand the section and enable the desired bot.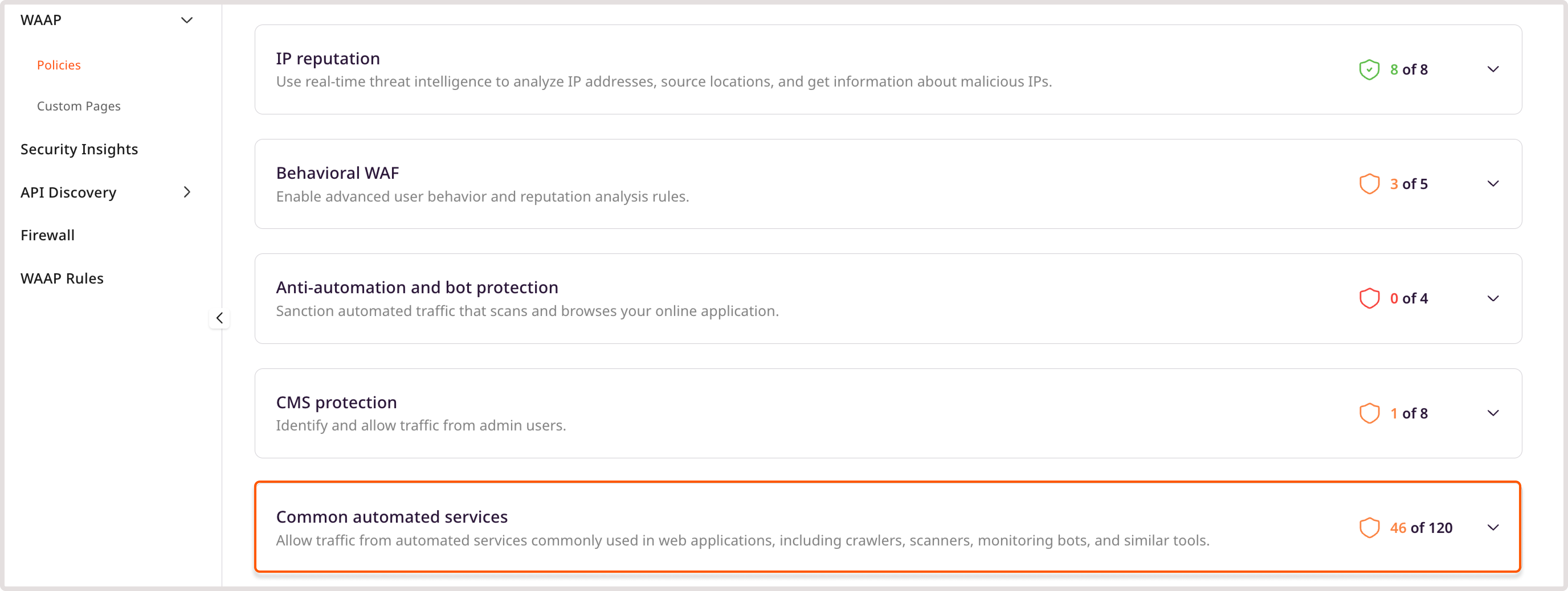
Step 7: Configure your APIs
If you plan to serve JSON requests through an API on your domain, you can disable the JavaScript injection and CAPTCHA functionalities for specified API endpoints. You can manually add endpoints to API base path or configure the API Discovery feature to automatically detect and protect your APIs.Step 8: Enable protect mode
1. In the Gcore Customer Portal, navigate to WAAP > Domains. 2. Find the needed domain and click its name to open it. You’ll be directed to the Policies page. 3. In the sidebar, click WAAP. 4. In the upper-right corner of the screen next to WAAP mode, select Protect. The WAAP will begin to inspect and act upon incoming requests.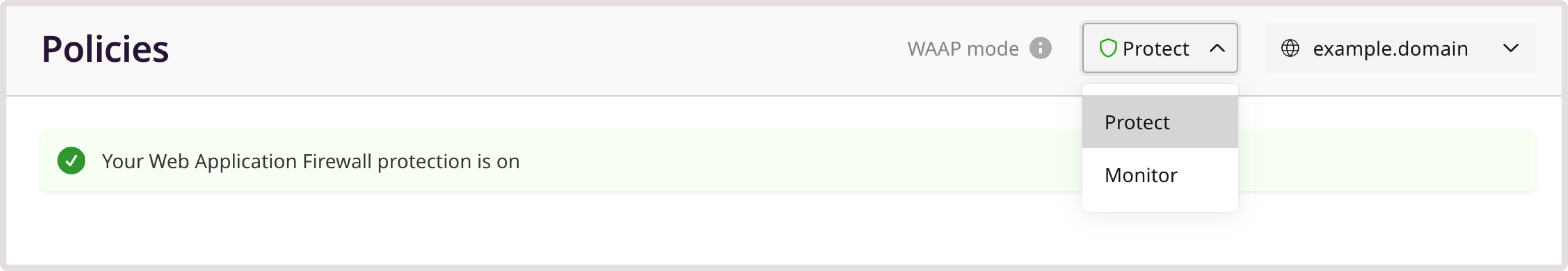
Step 9. Block non-GCore traffic
After successful DNS propagation and verifying that domain-based traffic is being handled by WAAP, ensure that all requests to your domain are routed through Gcore servers. This is necessary to prevent unauthorized traffic from bypassing WAAP and directly reaching your domain.- Add our CDN servers to the allowlist.
- Block other incoming requests that don’t match our allowlist.

